The convenience of modern vehicle entry systems, from remote keyless entry (RKE) to passive keyless entry (PKE) – also known as smart key systems or passive entry passive start (PEPS) – is undeniable. However, this technological advancement also opens doors for sophisticated car theft methods, making robust security solutions more crucial than ever. As experts in automotive repair at keyfobprog.com, we’ve seen firsthand the evolution of these systems and the increasing ingenuity of Key Fob Hackers.
Ultra-wideband (UWB) technology is emerging as a promising defense against these threats, offering enhanced security compared to Bluetooth and RFID. UWB’s ability to precisely measure distance makes it significantly harder to exploit through relay attacks, a favored tactic among car thieves.
In this article, the first of a two-part series, we will delve into the history of vehicle entry technology and examine common security breaches like replay attacks, rolling attacks, and relay attacks, as well as effective ways to mitigate them. We’ll also discuss recent reports highlighting potential vulnerabilities in systems like Tesla’s keyless entry, exploring how these systems can be exploited. In the second part of this series, we will take an in-depth look at UWB technology, its applications in vehicle security, and its potential weaknesses.
The Journey of Vehicle Entry Systems: From Keys to Key Fobs and Emerging Threats
Vehicle entry systems have come a long way from simple mechanical keys. Initially, basic keys were the standard, but their mechanical nature made them susceptible to duplication by experienced thieves. The late 1980s saw the introduction of remote keyless entry (RKE) systems, a significant step forward in convenience. Drivers could now unlock their cars with the push of a button. However, this convenience came with new security vulnerabilities. RKE systems became targets for signal jamming, replay attacks, and signal interception techniques employed by key fob hackers.
The next major innovation was smart key systems, enabling keyless entry and push-button start functionality. This advancement, while enhancing user experience, unfortunately introduced new attack vectors. Relay attacks became a prevalent method for vehicle theft, as they allowed thieves to amplify and extend the key fob’s signal to the car, even when the key was not physically present. This rise in sophisticated attacks, particularly targeting luxury vehicles, led to a surge in insurance premiums as these high-end cars became prime targets for key fob hackers. The escalating threat landscape underscored the urgent need for more secure entry systems, driving the industry towards technologies like ultra-wideband (UWB) for enhanced precision and security.
Beyond wireless technologies like RKE and PKE, Radio Frequency Identification (RFID) is also commonly integrated into modern vehicles. RFID can be used in physical key cards or virtual cards stored on smartphones. RFID systems offer a degree of security due to their short operational range, typically unlocking cars only when the card is within centimeters of the reader. This proximity requirement makes them inherently more secure during direct user interaction. However, even RFID systems are not immune to vulnerabilities. They can be susceptible to jamming by stronger signals on the same frequency, interception (“sniffing”) of communication between the tag and reader, and cloning, where the RFID tag’s identification code is duplicated to create a counterfeit.
Decoding Signal Attacks: How Key Fob Hackers Exploit Entry Systems
We’ve touched upon various signal attacks targeting RKE systems. Let’s delve deeper into how these attacks actually work and how key fob hackers execute them.
A jamming attack is essentially a denial-of-service (DoS) attack. In this scenario, hackers transmit radio signals with higher power, effectively overpowering the legitimate signal from the key fob. This prevents the vehicle from receiving the correct unlock signal.
Figure 1. A jamming attack
In a replay attack, key fob hackers intercept and record the signal transmitted from the legitimate key fob. They then re-transmit this captured, fixed-code signal to gain unauthorized access to the vehicle.
Figure 2. A replay attack
A rolling jam attack is a more sophisticated technique combining signal interception and jamming. Hackers simultaneously intercept the key fob’s signal while also jamming signals near the car. This jamming prevents the car from receiving the legitimate signal, tricking the car owner into pressing the key fob button multiple times. The key fob hackers capture these subsequent signals, which can then be used in future replay attacks. This method specifically targets vehicles equipped with rolling-code features, which are designed to prevent simple replay attacks by changing the code with each use.
Figure 3. A rolling jam attack
In a relay attack, key fob hackers utilize two radio devices. One device is positioned near the vehicle, while the other is placed in proximity to the victim’s key fob, which could be inside their home or pocket. These devices work in tandem to extend the key fob’s signal range. The device near the key fob picks up its signal and relays it to the device near the car. This effectively tricks the vehicle into believing the key is nearby, allowing the key fob hackers to unlock and even start the car.
Figure 4. A relay attack
These attack methods have proven to be effective in circumventing the vehicle entry systems we’ve discussed. Table 1 summarizes different types of vehicle entry systems and the associated attack methods that key fob hackers can deploy against them.
| Vehicle entry system | Potential attacks |
|---|---|
| Physical key | Hot-wiring |
| Remote keyless entry (RKE) | Jamming, replay, rolling jam |
| Passive keyless entry (PKE) | Relay |
| RFID (key card) | Jamming, sniffing, cloning |
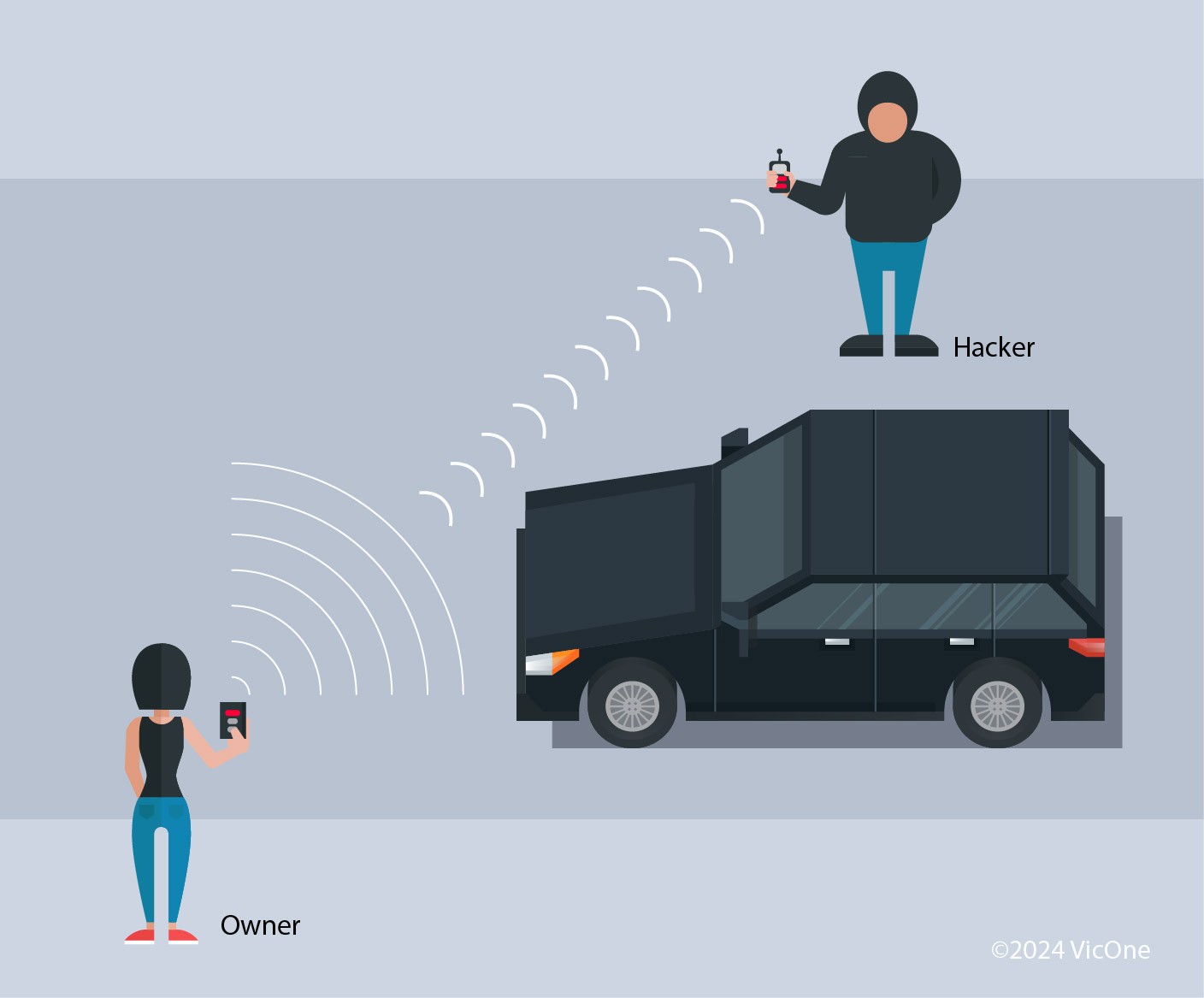
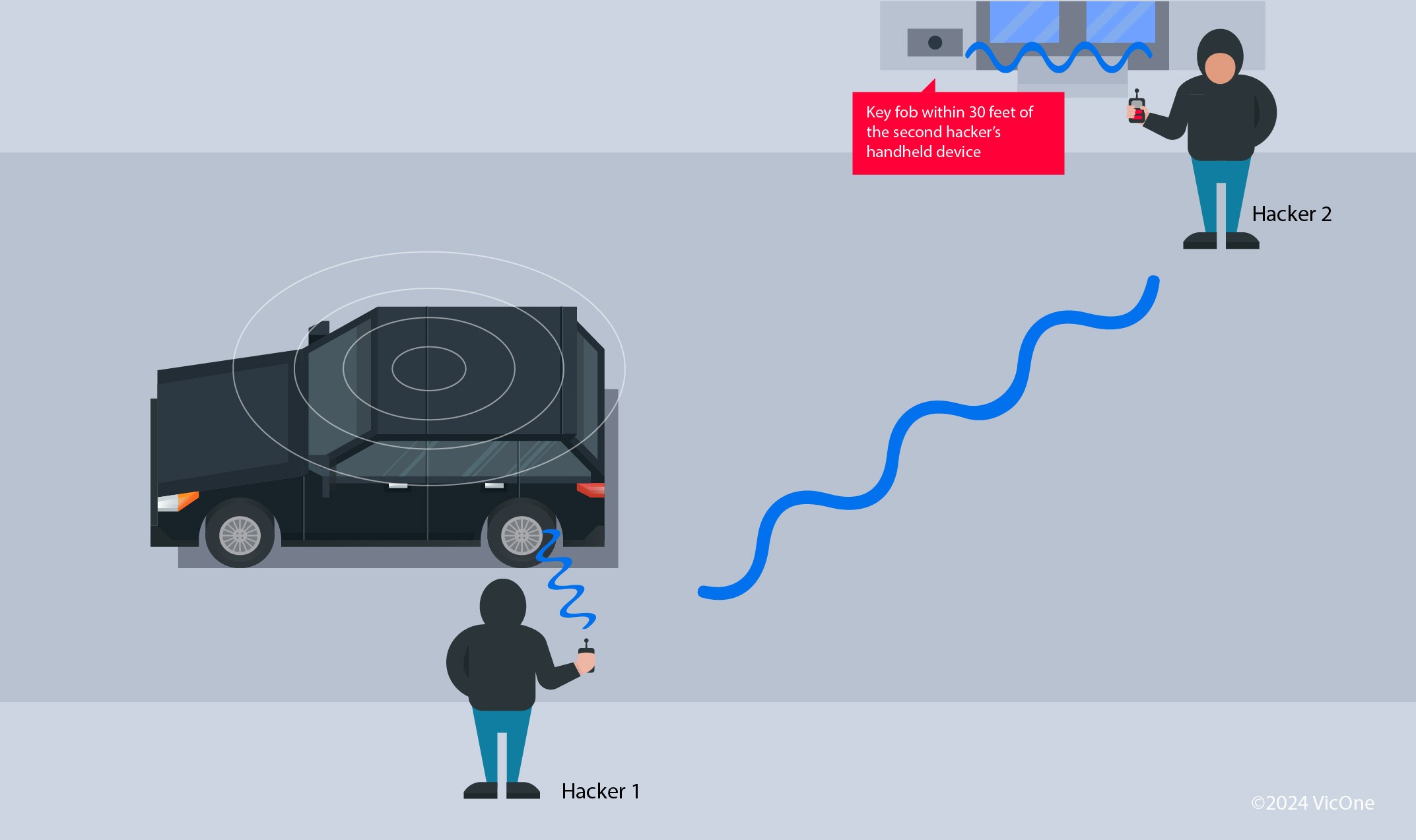
Table 1. Vehicle entry systems and common attacks by key fob hackers
Tesla Model 3 and UWB: Are Key Fobs Still Vulnerable?
UWB technology is heralded as the next major advancement in vehicle entry systems, promising to be a game-changer in security. This naturally leads to the question: How effective is UWB against current radio hacks, and can it truly deter key fob hackers? A recent report analyzing the Tesla Model 3’s implementation of UWB provides valuable insights.
The report, based on research from GoGoByte, indicates that while the Tesla Model 3 does incorporate UWB technology, it isn’t yet fully leveraging its distance-checking capabilities to prevent relay attacks. Tesla’s keyless entry system still primarily relies on Bluetooth for unlocking the vehicle and controlling the immobilizer. As a result, relay attacks via Bluetooth remain successful, mirroring vulnerabilities seen in earlier models. This means that even with UWB hardware present, key fob hackers can still exploit Bluetooth weaknesses.
Tesla has acknowledged these concerns and stated they are actively working to enhance UWB reliability and security. Until these improvements are fully implemented, Tesla vehicles remain susceptible to relay attacks. Despite this vulnerability, it’s worth noting that Tesla vehicles are reported to be among the least stolen vehicles in the US, largely attributed to their standard GPS tracking features. This inherent tracking capability provides a layer of security even if the car is stolen by key fob hackers.
To further mitigate risks, Tesla owners are advised to utilize the “PIN-to-drive” feature, which acts as a robust form of multifactor authentication (MFA). This security measure requires drivers to enter a four-digit PIN code before the car can be driven, even after it has been unlocked with a key fob or smartphone. PIN-to-drive adds a crucial second layer of protection, ensuring that even if a thief manages to unlock the car via a relay attack, they cannot start the vehicle without knowing the PIN. This feature serves as an effective interim safeguard against current security gaps until more robust UWB security measures are in place to truly combat sophisticated key fob hackers.
This report effectively highlights the current state of UWB implementation and emphasizes the ongoing need for improvements to fully realize its security potential. In the second part of this blog series, we will delve deeper into UWB technology, examining its security implications for vehicles and its future role in protecting against key fob hackers.